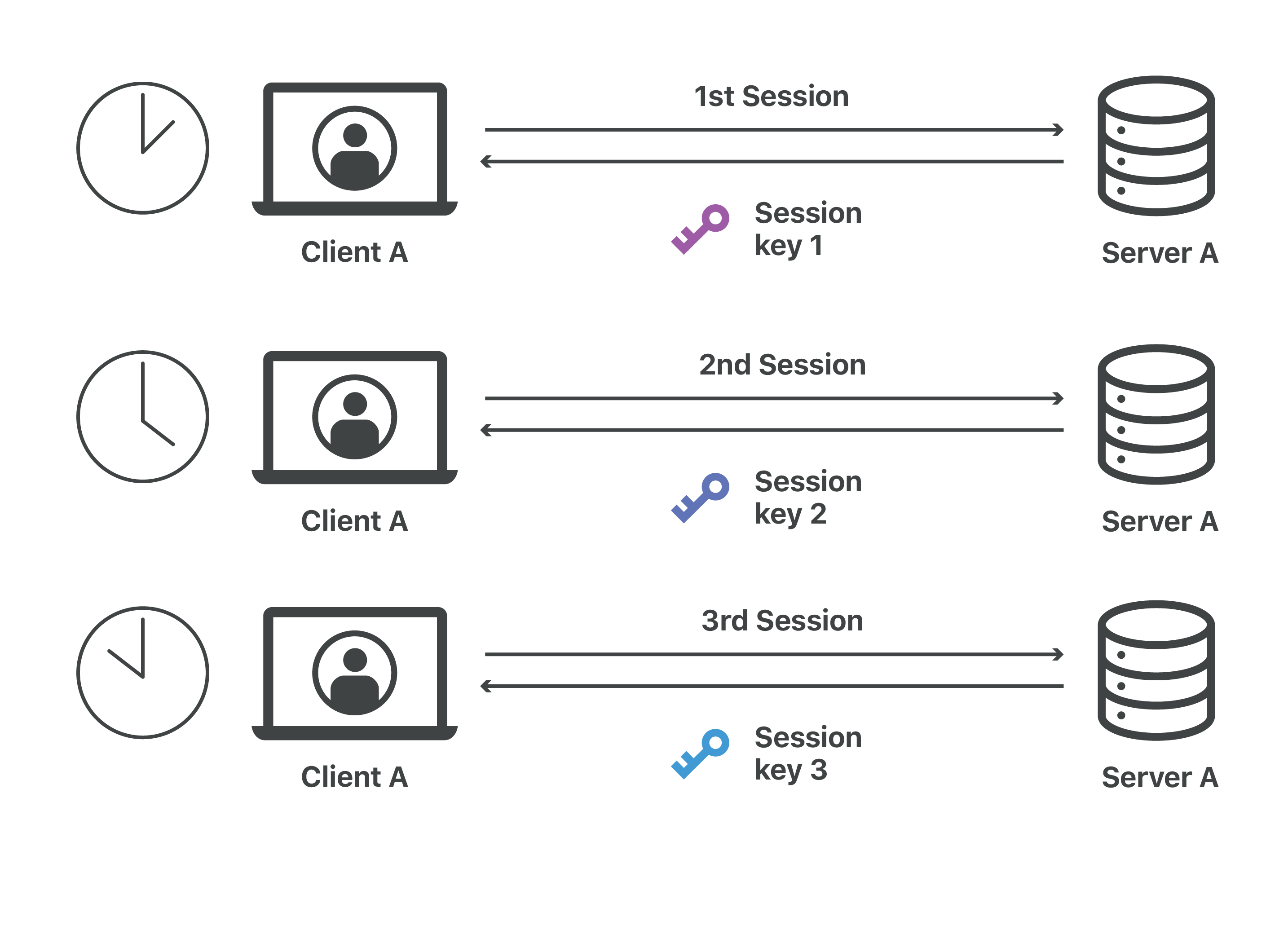
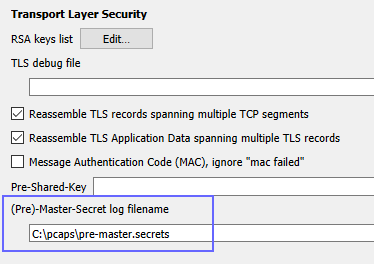
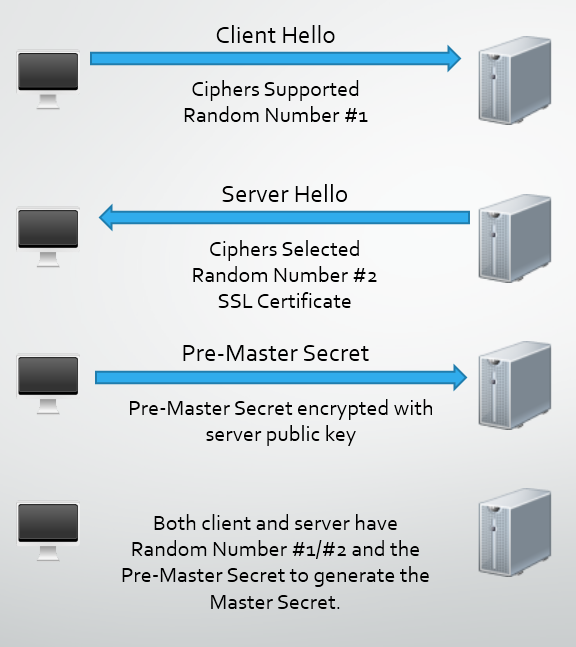
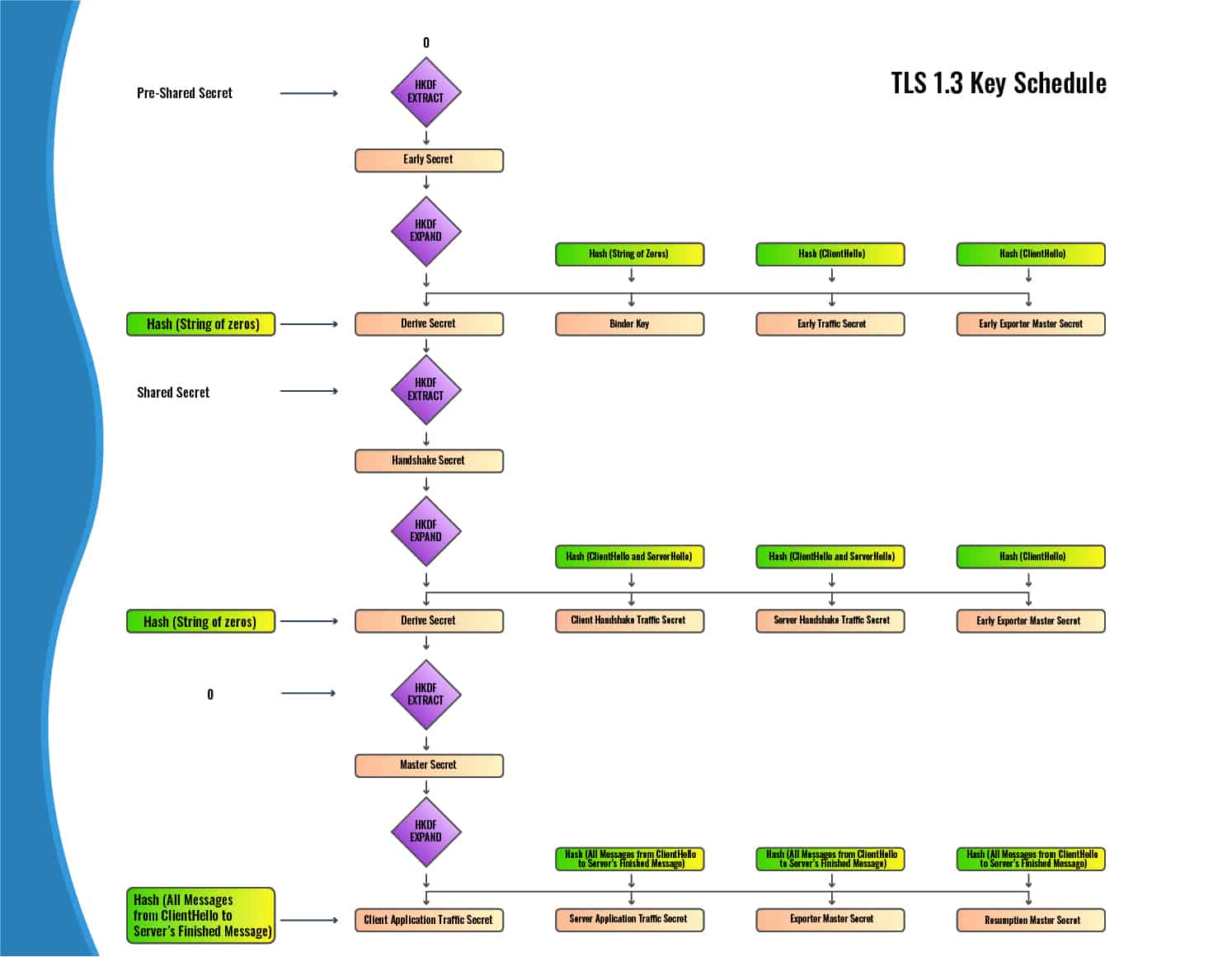
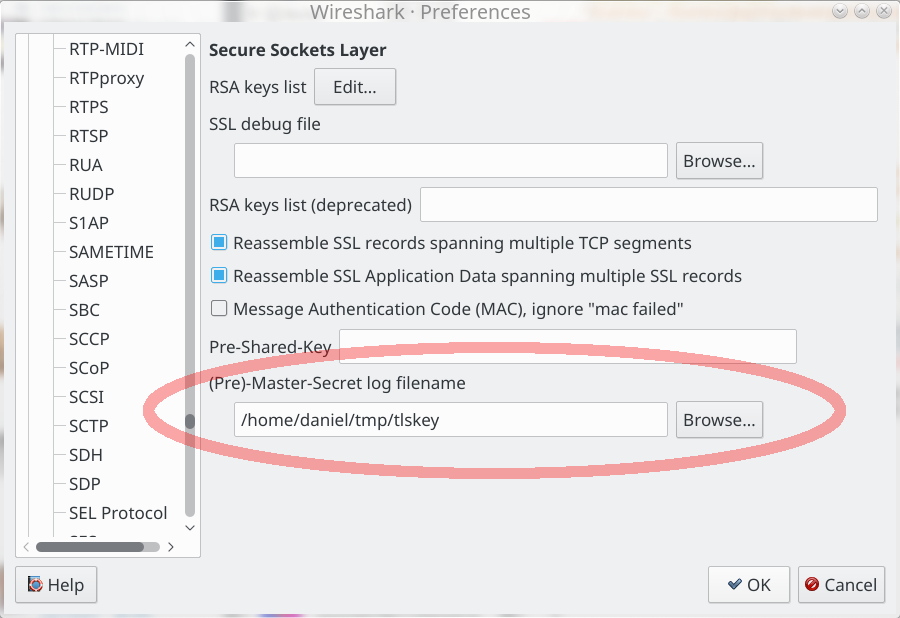
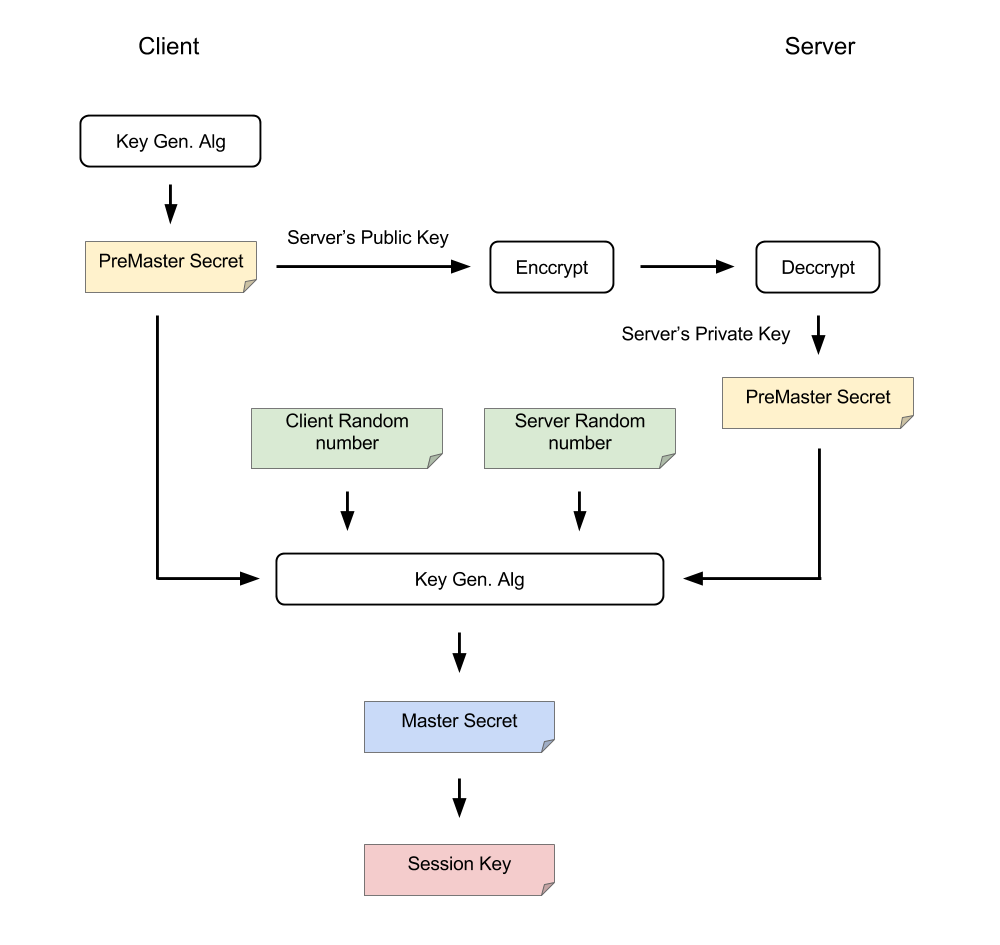
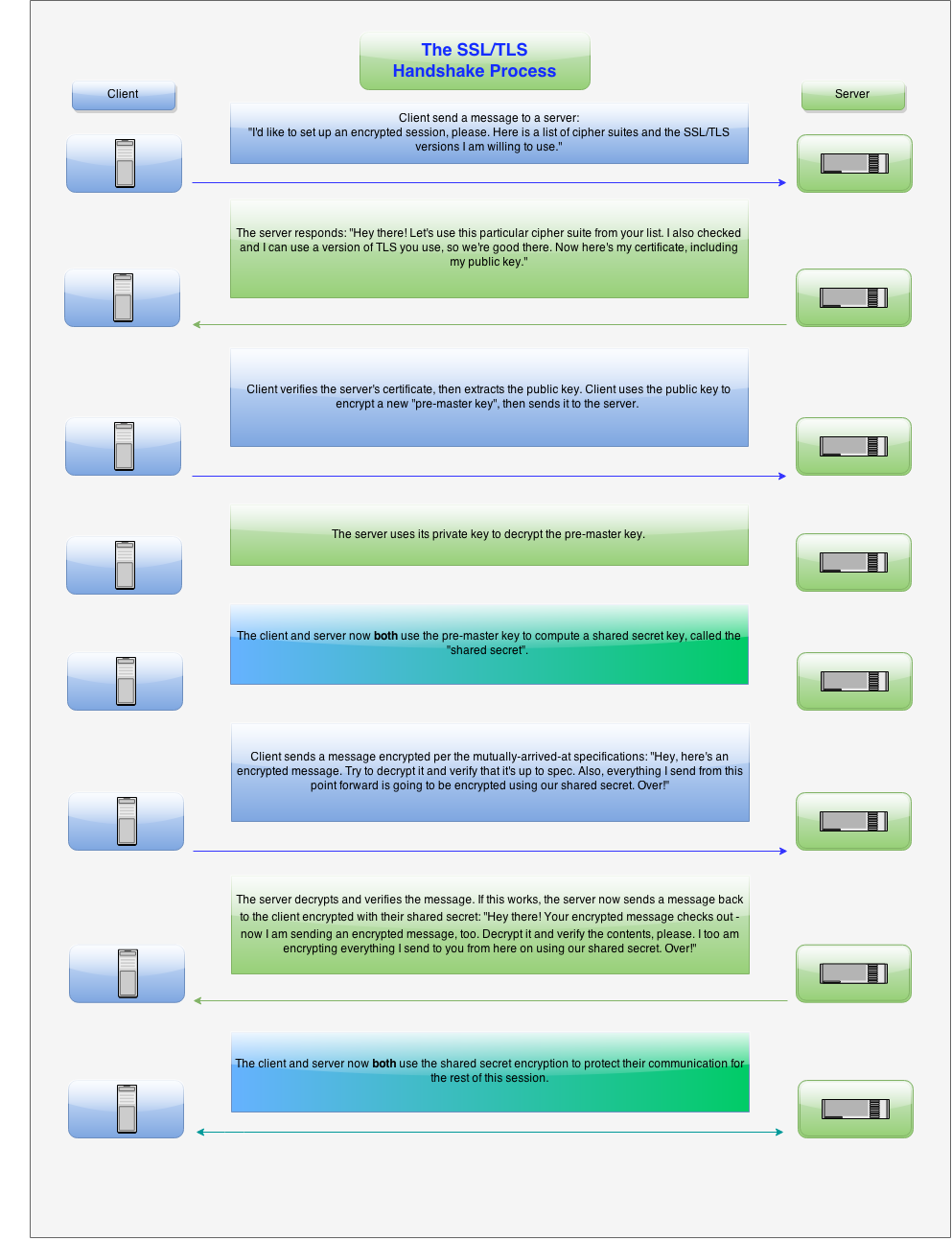
tls - Differences between the terms "pre-master secret", "master secret", "private key", and "shared secret"? - Cryptography Stack Exchange
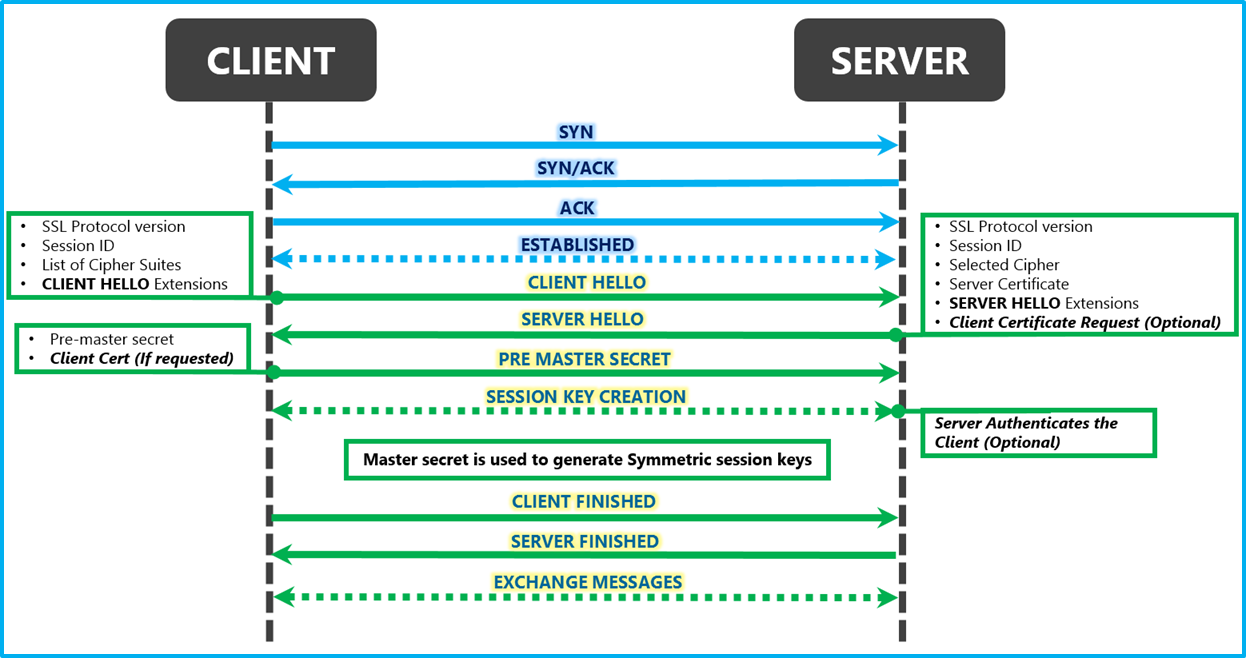
An overview of the SSL Handshake. In this post I will give an overview of… | by Robert van Rijn | Medium

Secure connections with TLS and Java | by alessandro battistini | The Hotels.com Technology Blog | Medium