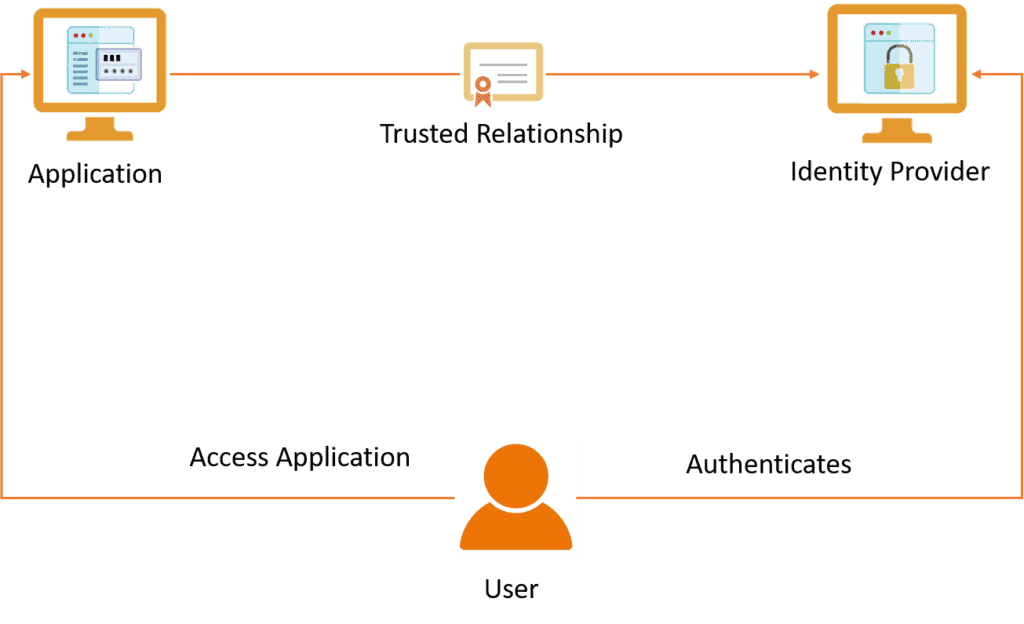
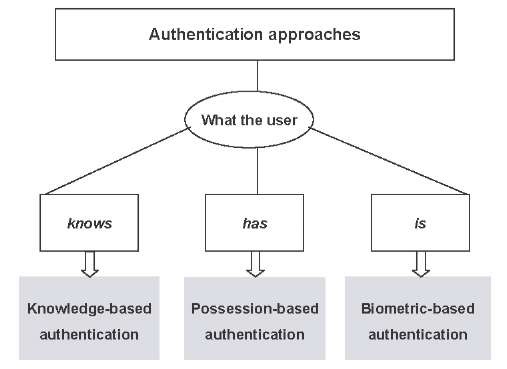
Pin by MAYLANCER TECHIOS on OUR SYMBOLISATION | Biometric authentication, Biometrics, Computer science
A Lightweight Three-Factor User Authentication Protocol for the Information Perception of IoT - UNT Digital Library

An authentication and key distribution system for open network systems | ACM SIGOPS Operating Systems Review

Authentication Security Vector Illustration Via Phone Or Computer For Code Message Shield And Password Secure Notice Login Stock Vector Image & Art - Alamy

Computer Science Lesson 35 Internet Terms (Apps And Applets, Encryption and Authentication, Port) - YouTube
Computer Icons Font Awesome Lock Multi-factor authentication Information, lock, information Technology, computer Science, business png | PNGWing

Lecture Notes in Computer Science Ser.: Advances in Biometric Person Authentication : International Wokshop on Biometric Recognition Systems, Iwbrs 2005, Beijing, China, October 22-23, 2005, Proceedings by Gérard Chollet (2005, Trade Paperback) for ...

Multi-Factor Authentication: How and Why You Should Protect Your Data | Multi factor authentication, Cyber security technology, Cybersecurity infographic

Springerbriefs in Computer Science: Mobile Authentication: Problems and Solutions (Paperback) - Walmart.com - Walmart.com